What is Phone-Centric Identity?
Phone-Centric Identity, also known as Mobile Identity, Device Intelligence, or Phone Intelligence, refers to technology that leverages and analyzes mobile, telecom, and other signals for the purposes of identity verification, identity authentication, and fraud prevention.
Phone-Centric Identity Signals Are Highly Correlated to Digital Trust
Phone-Centric Identity relies on billions of signals from authoritative sources pulled in real time, making it a powerful proxy for digital identity and trust. If you think about how many people have mobile phones, how long they have had them, and how often they use them, it’s clear why Phone-Centric Identity signals are highly correlated with identity and trustworthiness.

The above chart from a McKinsey report entitled “Fighting Back Against Synthetic Identity Fraud” shows that profiles with higher depth (how far back the data goes) and consistency (how often the same data is seen) had a lower risk of being fraudulent. Phone-Centric Identity™ signals—which include phone line tenure; phone behavior such as calls, texts, logins, and ad views; phone line change events as ports, snap-backs, true disconnects, and phone number changes; phone number account takeovers such as SIM swaps; and velocity and behavior of change events—are both high-depth and high-consistency.
For example, Phone-Centric Identity signals for a given consumer typically go back many years (high-depth), given that most consumers now open phone accounts at a relatively young age. In fact, 50% of 11-year-olds now have a phone number (Source: The Common Sense Census: Media Use by Tweens and Teens). In terms of consistency, Phone-Centric Identity™ signals provide one of the best views into whether a consumer’s activity is inconsistent with their regular activity, signaling potentially suspicious behavior.
This stands in stark contrast to social security numbers or passwords, which can be easily purchased on the dark web by hackers and used to break into a consumer’s account. In order to break Phone-Centric Identity™-based verification and authentication, a fraudster would need to buy a phone in the victim’s name, pay for it for years, and use it to make calls and log into apps every day to mimic the victim’s behavior. While this is possible, it certainly isn’t scalable or worth most criminals’ time.
The Unique “Possession” Factor
Phone-Centric Identity also uniquely utilizes the mobile device as a “what you have” factor that companies can use to deterministically say whether they are interacting with their customer or not. This check, often referred to as a “possession” check, returns a binary result as opposed to a probabilistic score. By understanding whether a consumer is in physical possession of their mobile device or not, Phone-Centric Identity technology can return a yes or no answer about whether a company is interacting with their customer or someone else.
Enhanced Customer Experience and Privacy
Phones also have built-in, passive authentication, encryption, and privacy. By applying Phone-Centric Identity technology to web, app, mobile, chat, call center, and even in-person interactions, companies can give their customers a safer, easier, and faster experience. The consumer does not need to download a separate app or purchase a physical hardware token to authenticate themselves, and the process can often take place invisibly and seamlessly through their existing mobile device.
Opening new accounts, logging in, resetting passwords, moving money, or calling a contact center for support can all feel as effortless as sending a text or making a phone call. Contrast that feeling to the one your customers experience when they need to answer security questions or fumble with easy-to-forget passwords, and it’s easy to see why Phone-Centric Identity™/Mobile Identity is becoming the modern and preferred way to prove identity.
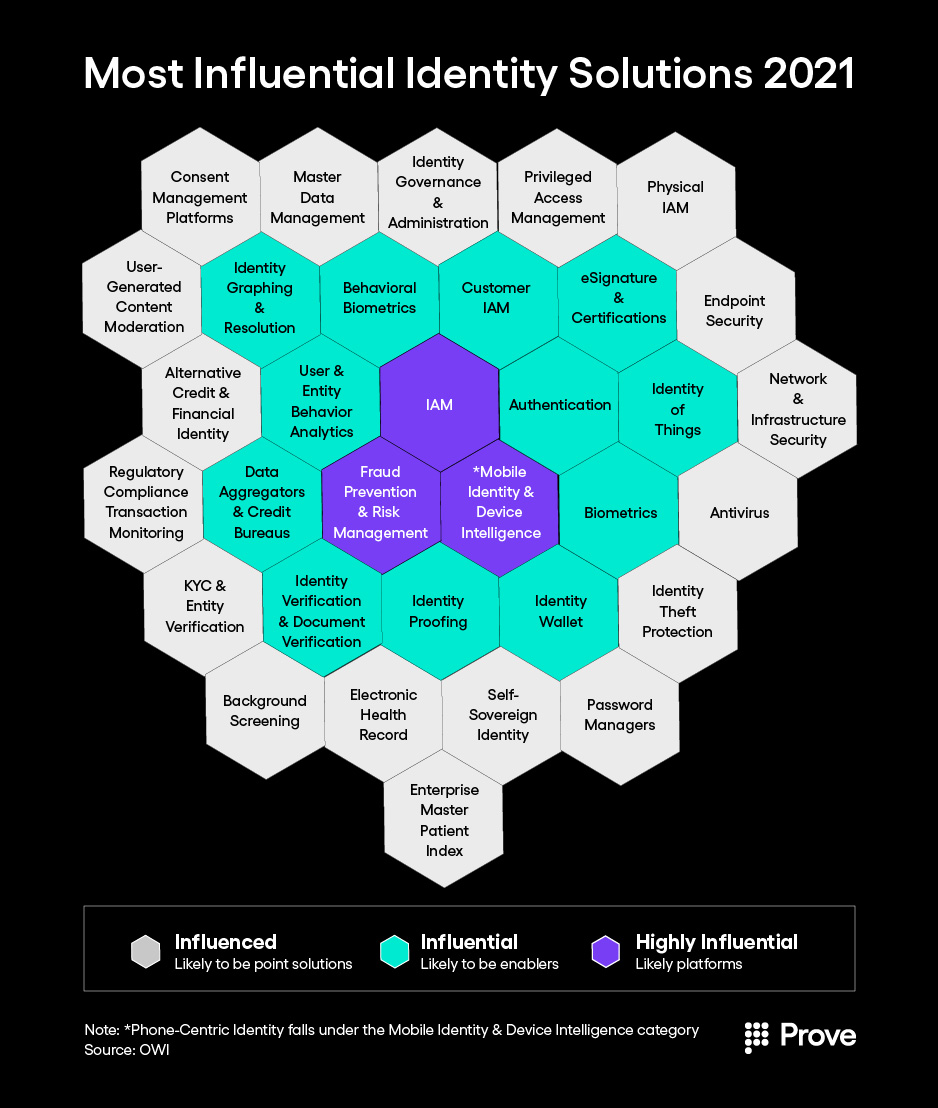
Growth and Influence of Phone-Centric Identity
Phone-Centric Identity and Mobile Identity/Device Intelligence are rapidly becoming the technology of choice for companies looking to verify and authenticate their customers in a secure fashion that does not hinder the customer experience. One World Identity (OWI) highlighted this space as highly influential in its January webinar on the 2021 Digital Identity Landscape:
“We’re seeing that become more and more relevant,” said Cameron D’Ambrosi, Managing Director of OWI. “Being able to rely on that device as a proxy for a human—especially a mobile device—because how many of us are attached at the hip to our smartphones all day every day? Both in terms of the velocity of those data attributes that we’re feeding into the digital identity ecosystem—making those extremely valuable—and the fact that when you lose your device or it’s stolen or taken over maliciously, you are probably going to recognize that very, very quickly as a consumer. And that makes this tremendously useful especially for these fraud and risk use cases.”
Later in the webinar, OWI specifically highlights Prove as a leader in the Mobile Identity and Device Intelligence space. Watch the whole webinar here.
How Phone-Centric Identity Works: 3 Checks Companies Should Be Using to Fortify Their Identity Verification & Authentication
While the signals that Phone-Centric Identity™ analyzes are complex, the concept is quite simple and boils down to three factors: Possession, Reputation, and Ownership:
- Possession answers the question: Is this customer in possession of the phone? Knowing that someone is in possession of a phone at the precise moment of a potential transaction helps identify someone regardless of the transaction channel and helps ensure the customer is indeed on the other end of an interaction.
- Reputation answers the question: Are there risky changes or suspicious behaviors associated with the phone number? Typically, people have had the same phone number for a long time and upgrade phones only every few years. Compare that to a burner phone, or a phone that underwent a SIM swap, or a phone number that was just registered. These activities lower the reputation of the phone itself, which allows companies to flag the phone regardless of the customer activity.
- Ownership answers the question: Is the customer associated with the phone number? It is crucial to associate a phone number with a person when confirming that the customer is in possession of the phone. Otherwise, the wrong person may be verified. This means knowing when a customer truly gets a new phone number or knowing that phone number is still associated with a person even if they switch carriers.
Companies can evaluate their own identity verification and authentication processes against the above checks to see if they are meeting the highest levels of security and identity certainty.
How can companies leverage Phone-Centric Identity and the PRO Model of Identity Verification & Authentication?
Phone-Centric Identity™ has many different applications, but some popular use cases include:
- Identity verification/identity proofing
- Seamless login authentication (two-factor authentication/multi-factor authentication)
- SIM swap fraud/account takeover prevention
- New account creation/user acquisition
- Authenticating call center calls
It’s also important to note that Phone-Centric Identity™ signals can be used not only for mobile interactions but also across web and call center channels.
As more companies shift to interacting with customers digitally, this “PRO” model of identity is gaining more awareness as a modern alternative to legacy identity verification methods. It is not only a more secure identity model but also enhances the customer experience. With phone-based authentication, companies have the opportunity to change the customer experience from clumsy to seamless. They are able to use dynamic, encrypted signals to mitigate fraudulent activity in real time. And, more importantly, they are able to approve more legitimate customers in real time, helping those customers do just as much, if not more, online as they would be able to in-person.
Interested in learning how Phone-Centric Identity can improve your identity verification strategies to make your customer experiences safer, faster, and easier?
Prove is the modern platform for Phone-Centric Identity™ and is used by over 1,000 enterprises and 500 financial institutions, including 9 of the top 10 US banks. Get in touch with us to learn how we can help you accelerate revenue, mitigate fraud, and reduce OPEX with our proven approach to identity verification and authentication that is tied to the phone and the phone number.
Get in touch

Keep reading

Prove’s solutions can help businesses make their online customer experiences faster, easier and more secure.

While the rise of deepfake technology is not totally new, its level of sophistication presents new challenges for businesses seeking to deliver frictionless digital onboarding experiences to their customers.

Prove and BetMGM, the sports betting and iGaming leader, have entered into a partnership which will elevate the security standards and user experience for BetMGM customers through the Prove Pre-Fill® identity solution.














