Key Integration Considerations When Choosing an Identity Verification Platform

Identity verification (IDV) is a key defense against fraud. Many industries are legally required to confirm a person is who they claim to be, typically by checking their government-issued documents or biometric data, in compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations. Even when not required, IDV helps strengthen your business by improving security and customer trust.
However, whether it's required or not, building your own IDV solution isn't worth the risk. The complexity, legal requirements, and security challenges surrounding personally identifiable information (PII) make third-party platforms the smarter and safer choice.
If you're picking an IDV platform, this article covers what you need to know and focuses specifically on integration. We'll take a look at why integration should be a top priority when choosing an IDV platform and how to approach integration testing to ensure you choose a platform that accelerates, rather than hinders, your business goals.
Why Integration is a Critical Priority
When choosing an IDV platform, your primary concern should be the ease and quality of integration. The best fit results in a fast time-to-market, low maintenance costs, and minimum engineering work.
Integration bottlenecks often occur when platforms don't play well with your current systems. The following are some common compatibility issues:
- Poor integration with existing authentication and authorization systems.
- Lack of support for your preferred development frameworks and technologies.
- Missing tools and documentation needed for implementing, testing, and monitoring.
These integration issues directly impact the success of your implementation. Poor integration compatibility can lead to extended development cycles, increased costs, and potential security flaws.
API Design and Developer Experience Considerations
The API that you choose impacts developer experience, application performance, and scalability. While developer familiarity with a particular technology is a valid consideration, it's best to consider the trade-offs between different API paradigms.
REST vs. GraphQL vs. gRPC
While several API styles exist, a high-quality REST API is the industry standard for providing software-as-a-service (SaaS) integrations. REST APIs are widely understood by developers, and their use of familiar HTTP methods reduces development time and complexity.
When evaluating a provider's REST API, focus on quality indicators. A good API has the following characteristics:
- Concise set of endpoints: Too many endpoints can make the API difficult to navigate.
- Efficient data payloads: The API should return relevant data, not large, unnecessary payloads.
- Clear versioning and schema: Endpoints should be versioned, with well-documented schemas and meaningful error responses.
You may also encounter platforms offering GraphQL or gRPC:
- GraphQL lets clients request exactly the data they need in one call. Instead of making multiple requests to different endpoints, a GraphQL API handles the data aggregation and formatting for you, similar to how backend database queries work. However, this is overkill for typical IDV workflows, which are usually simple, isolated processes.
- gRPC is a high-performance protocol using HTTP/2 and Protocol Buffers (protobuf) for fast, efficient server-to-server communication. It supports continuous data exchange over a single connection, which can be useful for real-time use cases, like camera feeds. However, gRPC lacks strong browser support, making it impractical for client-side user verification in web applications.
Essential API Features: Idempotency and Retry Mechanisms
Beyond choosing an IDV platform that follows best practices, choose one that provides clear guidance on error handling and idempotency. This ensures failed requests can be safely retried without creating duplicate records or unintended consequences.
For instance, if a client sends a request but never receives a response, the user may retry the action. Without idempotency, this could result in duplicate verification cases. A reliable platform must recognize repeated requests for the same operation and ensure it's executed only once to maintain data integrity:
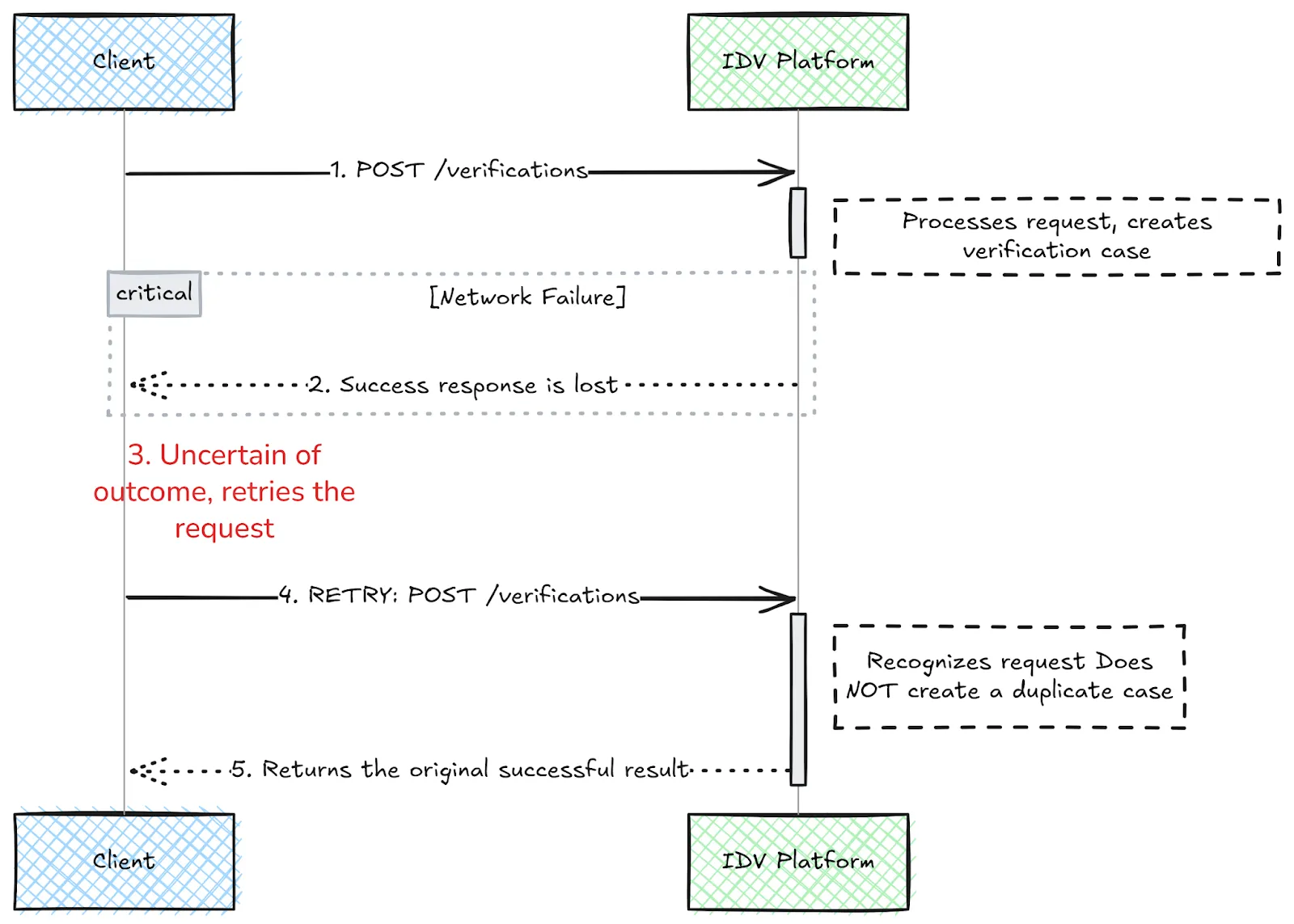
The IDV process is typically not instantaneous. It may involve complex, multi-step processes, like AI reviews, manual reviews, and third-party data checks, that take time. Keeping an open connection while waiting for these long-running tasks is inefficient and prone to failure.
A better approach is to use asynchronous jobs, meaning that when a client submits a verification request, the API immediately acknowledges that the request is being processed while the job runs in the background via the IDV platform provider. Upon verification completion, the IDV platform sends webhooks to notify your system. This push-based notification is far more efficient than maintaining an open HTTP connection or repeatedly polling the IDV platform for status updates:
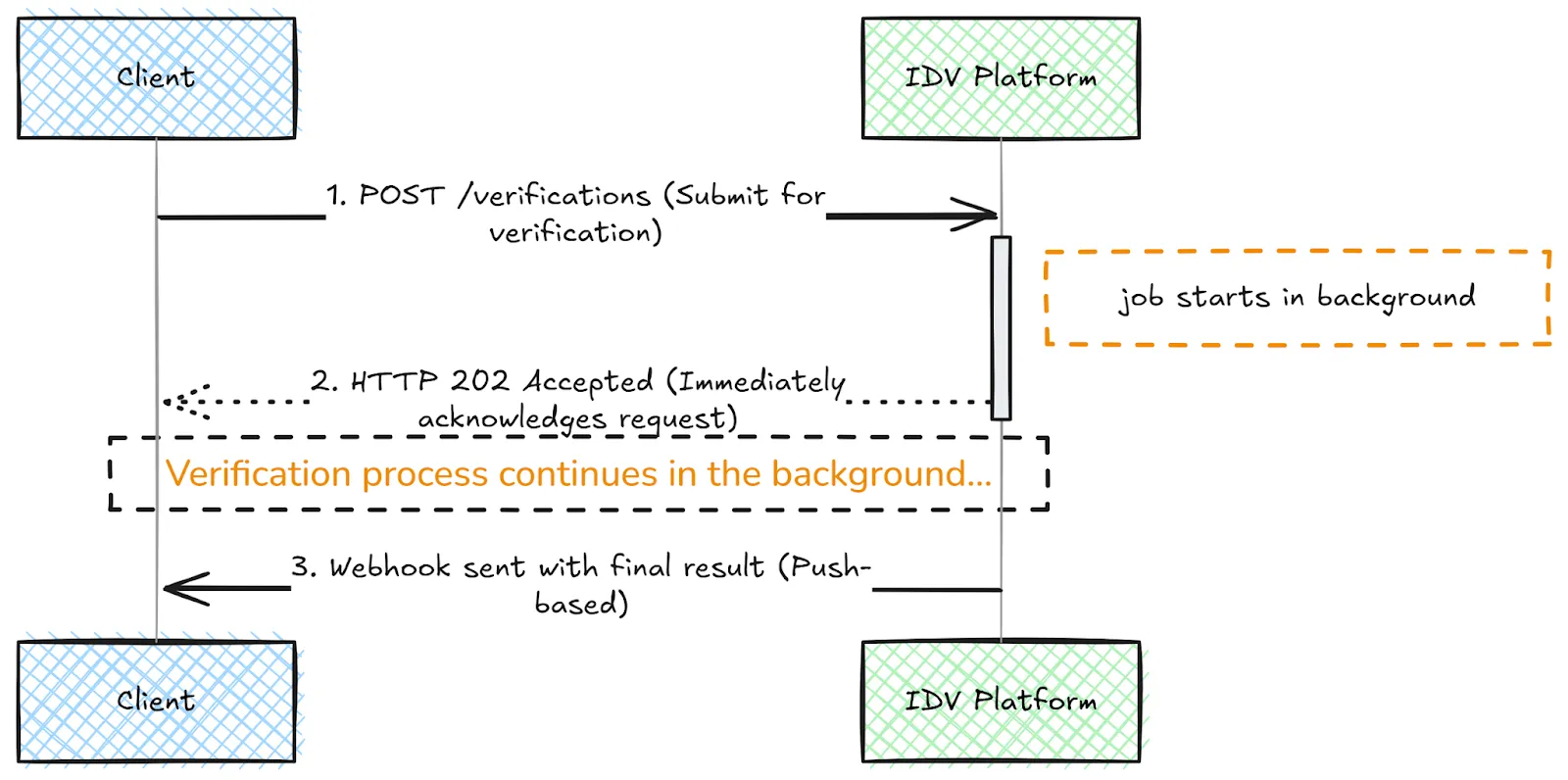
You should expect your IDV platform to support proper idempotency for all API endpoints, clear retry mechanisms, and asynchronous job processing with webhook notifications for long-running tasks.
Don't Skimp on SDK Quality and Client-Side Support
While API design is important, a strong SDK offering improves the developer experience by providing language-specific clients that developers can use without writing request-handling code. A comprehensive SDK should not only abstract away API integration but also offer prebuilt methods for common operations, such as handling authentication, errors, and retries.
An IDV platform's value is significantly enhanced if it offers seamless integration into your development ecosystem instead of just providing APIs. The breadth of the platform SDK support is often a good indication that it has a broad customer base and the ability to deliver integration in various programming languages. Here's what good coverage looks like:
- Backend: Java, Go, Node.js/TypeScript
- Mobile: iOS-specific (Swift/Objective-C) and Android (Kotlin/Java)
- Cross-platform: React Native, Flutter
Make sure the SDKs are public as this fosters trust and transparency and allows users to suggest changes if necessary.
If you want to reduce development overhead, choose platforms with client-side IDV integration and prebuilt UI components. Instead of requiring your developers to build dedicated user flows for document capture and data entry from scratch, the IDV provider can offer a fully tested, out-of-the-box workflow. This means the primary integration task is to customize the look and feel of these components to match the application’s branding.
Key considerations for a client-side SDK integration should include the following:
- Customizability: The SDK should allow for easy branding (colors, fonts, logos) to ensure seamless visual integration with the host application.
- Lightweight and performant: The prebuilt UI and underlying SDK must be optimized to have a minimal impact on the app’s size and performance.
- Clear versioning: Developers should be able to manage application updates without unexpected breaking changes in the workflow.
- Security: The SDK must ensure end-to-end security and integrate with your authentication system.
Security Integration Concerns
Security is crucial in IDV because it involves handling sensitive user data. While API communication generally uses API keys and follows standard security workflows, two integration points require special attention:
- Client-side workflow: The client-side environment, such as a user's browser, is not secured for credentials like API keys. For this reason, these workflows require different security measures, such as an authentication workflow.
- Asynchronous verification process: The service that receives the external webhook must ensure the response is genuine and cannot be forged or tampered with.
Secure the Client-Side Workflow
To secure the client-side workflow, you need a reliable, tamper-proof link between the user’s session, the IDV process, and any webhook callbacks for asynchronous flows. This requires the IDV provider to integrate with existing auth mechanisms, such as OAuth 2.0, OpenID Connect (OIDC), or Security Assertion Markup Language (SAML), so your platform can delegate verification while maintaining a consistent authentication framework.
Secure the Webhook Callback
Securing the webhook callback usually involves two lines of defense. The first is token-based authentication, meaning each webhook must have a specific header with a secret token as a value. The request should be dropped if the header is missing or the secret is invalid.
The second layer is called signature verification, which ensures the authenticity and integrity of webhook messages by verifying that they haven't been tampered with. The signature is provided via a second header, which is computed using a hashing algorithm (like HMAC-SHA256) applied to the webhook payload. This signature should be verified on your end using a shared secret key to ensure the message's authenticity.
Your IDV provider should provide these two layers of security in their asynchronous workflow and also offer simple ways to rotate both the webhook secret token and signature secret:

Compatibility with Modern Architectures
Integrating with an IDV should be possible without compromising your microservice and cloud-native architecture's scalability, resilience, or maintainability.
Serverless and Edge Considerations
If you're using serverless or edge functions for webhook handling, performance is key. Cold starts, or those initial latency periods when your serverless environment starts after being idle for a while, lead to missed webhooks and failed verification processes. Your IDV platform needs robust retry mechanisms to handle these initial timeouts and ensure guaranteed delivery.
Event-Driven Systems
Modern architectures commonly use event-based workflows with message systems, like Apache Kafka, Amazon Simple Notification Service (Amazon SNS) / Amazon Simple Queue Service (Amazon SQS), or RabbitMQ. While direct integration between your IDV provider and messaging system might seem ideal, most IDV platforms don’t offer this capability due to the complexity of supporting numerous messaging technologies.
The standard approach uses a dedicated ingress service or API gateway to receive IDV webhooks. This service’s sole responsibility is to authenticate the request (via a secret token and signature verification) and then place it onto a message bus. Even with this setup, guaranteed delivery from your IDV provider is essential for handling outages on your end:

Multi-tenant and Global Applications
As your business scales, your integration needs become more complex. New concerns come into play if you serve multiple independent customers (multi-tenancy) or customers across the globe.
A platform supporting multi-tenancy must provide a tenant-aware API, meaning that the endpoint or payload offers an error-proof way to identify which tenant an API call is for. This is critical for ensuring that data is strictly segregated for each of your customers.
For global applications, data residency is a main concern. Data privacy laws like the EU General Data Protection Regulation (GDPR) require that citizens’ personal data be stored and processed within a specific geographic region. A compliant IDV provider must have a global infrastructure and allow you to select the appropriate data center, such as EU, US, or APAC, to process and store data for your users.
Look for providers who can prove their commitment to security with independent certifications. A SOC 2 certification, for instance, would ensure that your IDV provider has undergone a rigorous third-party audit of their security, privacy, and confidentiality.
Testing and DevOps
IDV platforms without proper testing tools create unnecessary integration headaches. Without testing support, developers have to build their own mocks to simulate API requests and responses. Crafting these mocks is a time-consuming process that becomes nearly impossible without good documentation.
Your platform should provide a Swagger OpenAPI Specification (OAS) with detailed request and response examples. Even better is to provide mock APIs or servers with rich test data and scenarios built in. This lets developers test against preexisting data sets and confirm their integration is successful.
For continuous deployment, you need a high-fidelity sandbox environment that replicates the production system. This means full workflow testing from client-side integration to asynchronous webhooks, enabling end-to-end testing in your user acceptance testing (UAT) environment. The sandbox should include additional endpoints for testing scenarios, like account resets, process validation, and failure simulation.
For performance and load testing, consider platforms that provide dedicated test data sets and performance testing tools. You need to validate how your integration handles load and stress before production deployment. The best providers offer automated test suites that integrate directly into your continuous integration, continuous delivery (CI/CD) pipeline, significantly reducing the manual testing burden.
Operational Considerations Post-Integration
Successfully launching the integration is not the end of the project. You need to ensure everything works smoothly and continue to monitor your system.
The most critical part of signing with a SaaS vendor is reviewing their service-level agreement (SLA). Make sure you review their uptime guarantee. What is their retry policy and delivery policy for webhooks in asynchronous processes? How do they handle client failures and ensure request idempotency?
Additionally, make sure you evaluate communication channels with your vendor:
- How will the IDV provider inform you of downtime?
- What are the fallback behaviors during outages?
- How can you get immediate support for production incidents?
- How does the IDV provider communicate releases and changelogs?
- What integration support do they provide?
Lastly, ask whether the IDV provider will provide you with logs, metrics, and traces from their side of the system. There’s nothing more frustrating than integrating with a black box, where you can’t investigate or get information about what’s happening on their side of the process.
Conclusion
Navigating IDV platform requirements and selecting the right provider can be daunting, but choosing the right platform can make all the difference. To help you navigate the decision, use the following chart:
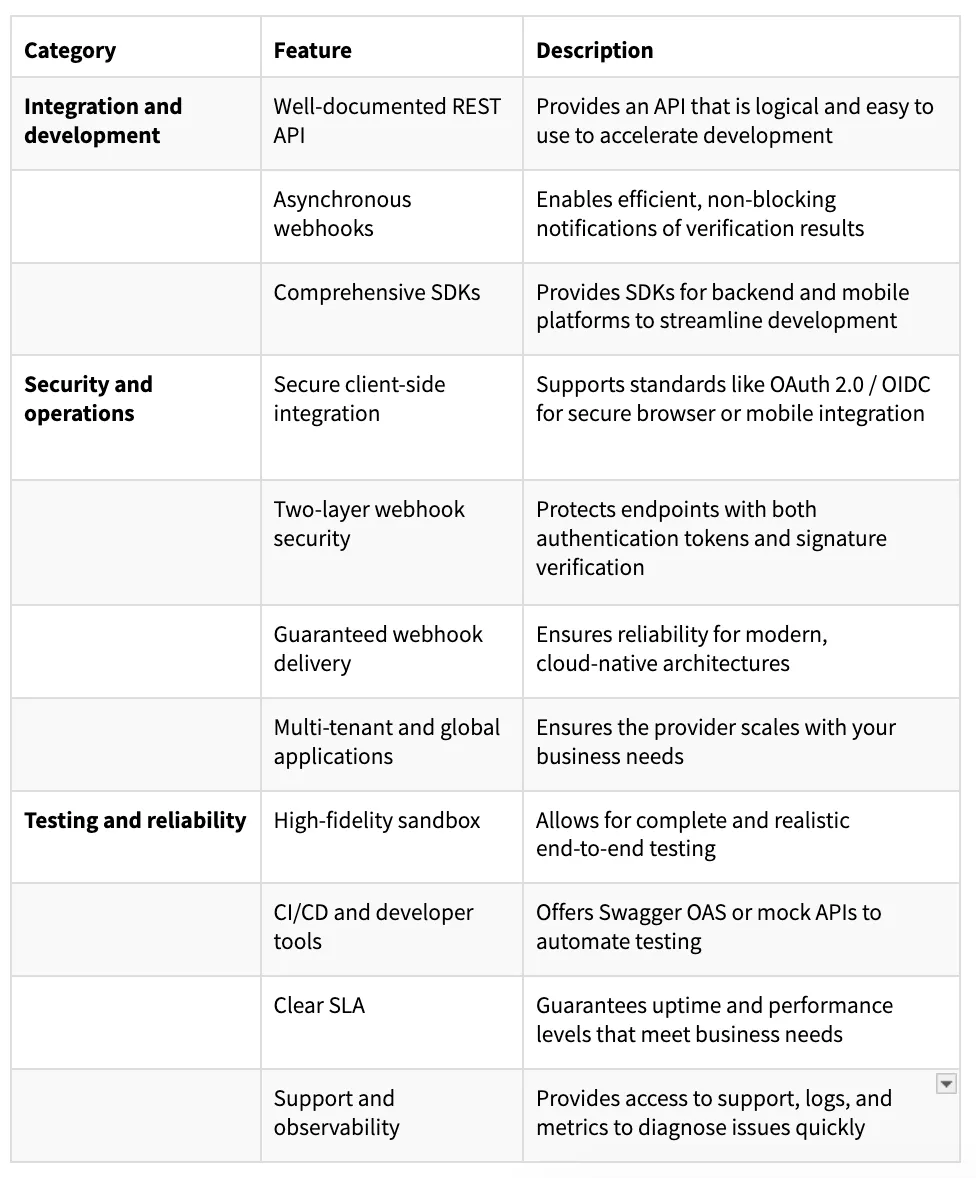
Prove simplifies IDV with developer-friendly APIs that handle the complexities of retry logic, idempotency, and error management automatically. This allows your team to focus on building features rather than managing infrastructure reliability.
Start building with Prove today—explore our API documentation or gain sandbox access.

Keep reading
 Read the article: Identity Has Been Redefined. Here’s What That Means Now.
Read the article: Identity Has Been Redefined. Here’s What That Means Now.In an era of deepfakes and automated fraud, traditional one-time identity verification is no longer enough. Learn why organizations must transition to continuous, adaptive identity systems to ensure security without sacrificing seamless user growth.
 Read the article: The Death of the OTP: Why Legacy MFA is Failing the Modern Consumer
Read the article: The Death of the OTP: Why Legacy MFA is Failing the Modern ConsumerDiscover why legacy MFA is failing and how Prove Unified Authentication provides a smarter, frictionless alternative. Learn how to replace insecure SMS OTPs with continuous, multi-layered identity assurance that prevents fraud while boosting conversion rates.
 Read the article: Prove Launches ProveX℠, the Internet’s First Digital Trust Exchange
Read the article: Prove Launches ProveX℠, the Internet’s First Digital Trust ExchangeProve launches ProveX, ProveX, a new digital trust exchange that enables enterprises to instantly access verified data and credentials from partners, while preserving trust through every interaction













