Why Top Banks and FinTechs Are Adopting Phone-Centric Identity for Frictionless PSD2 SCA

Phone-Centric Identity—it’s a buzz term that you may have been seeing more and more often, but what is it, and how are leading financial institutions using it to improve their customer experience, mitigate fraud? And how have top banks and FinTechs achieved the following kinds of real-world results using Prove’s Phone-Centric Identity™ approach?
- Replace the need for an OTP, removing the risk of social engineering
- Compliance with PSD2/SCA without hampering the customer experience
- 25% increase in day-one digital registrations
Phone-Centric Identity—sometimes called mobile identity, device intelligence, or phone intelligence—refers to technology that analyzes mobile, telecom, bank, and other authoritative signals for digital identity verification, authentication, and fraud prevention. It analyzes billions of real-time signals from authoritative sources. If you think about how many people have mobile phones, how long most adults have had mobiles, and how often they use them, it’s clear why Phone-Centric Identity signals are the most powerful proxy for digital identity and trust today.
In practice, many leading organizations have been shifting from more traditional identity models and adopting technology and intelligence such as our Phone-Centric Identity as a means to verify and authenticate customers and comply with regulations such as PSD2/SCA with as little friction as possible. This technology also uniquely utilizes the mobile device as a “what you have” factor that companies can use to deterministically say whether they are interacting with their customer or not. This check—also called a “possession” check—returns a binary result instead of a probabilistic score. By understanding whether a consumer is in physical possession of their mobile device or not, Prove can return a “yes” or “no” answer about whether a company is interacting with their customer or not.
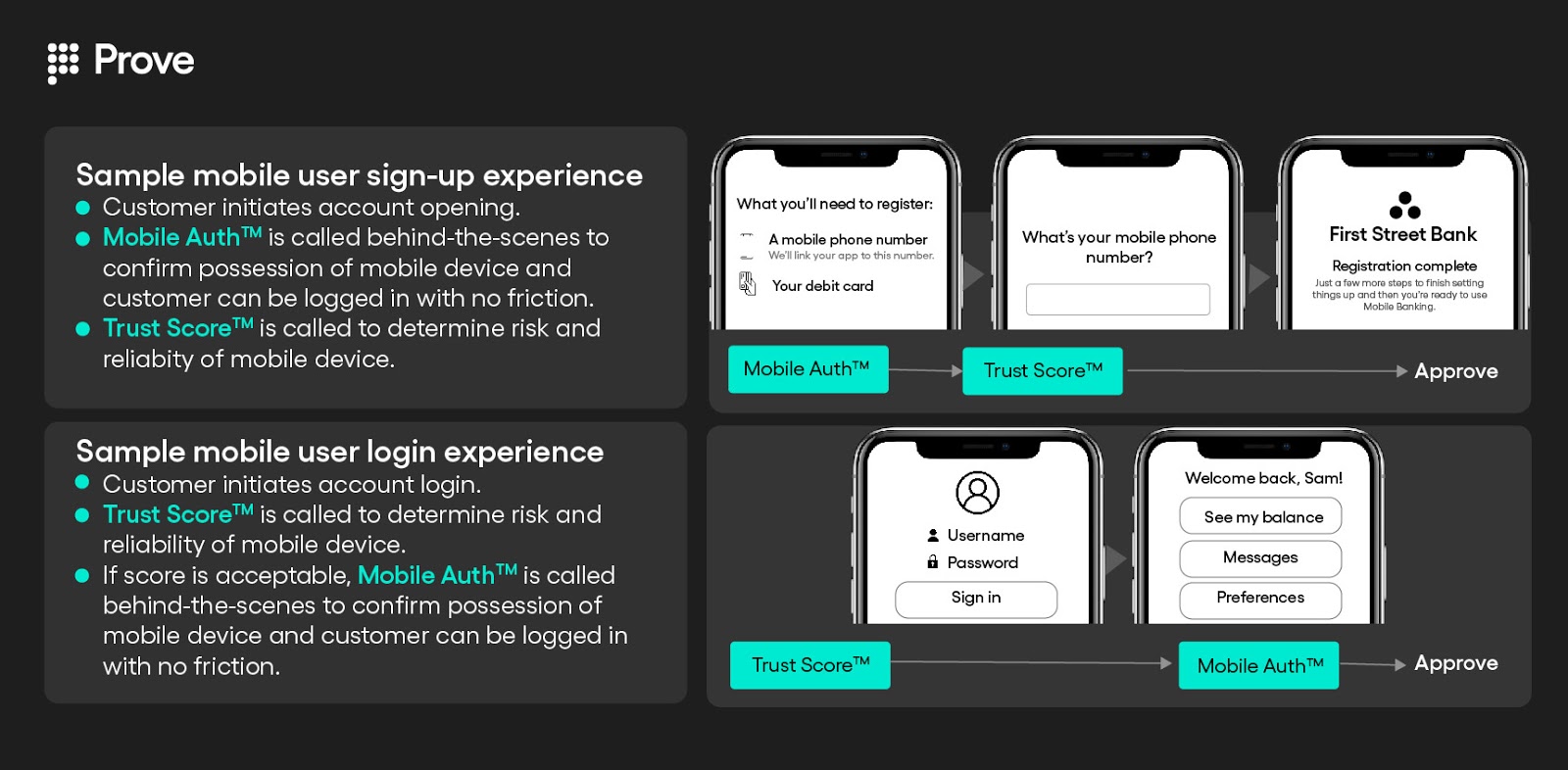
In addition to the real-world results seen above, leading banks and financial institutions have reported the following benefits with Prove’s Phone-Centric Identity approach:
- The ability to onboard more new customers more quickly to realize more revenue
- Faster and more accurate transaction decisioning (3DS 2.0) to improve exemption detection and reduced ‘step up,’ which also saves OPEX
- The ability to recognize your customer with one phone-number-based identity token across the entire customer journey and to manage changes to your customer phone numbers so that you always have the most up-to-date information
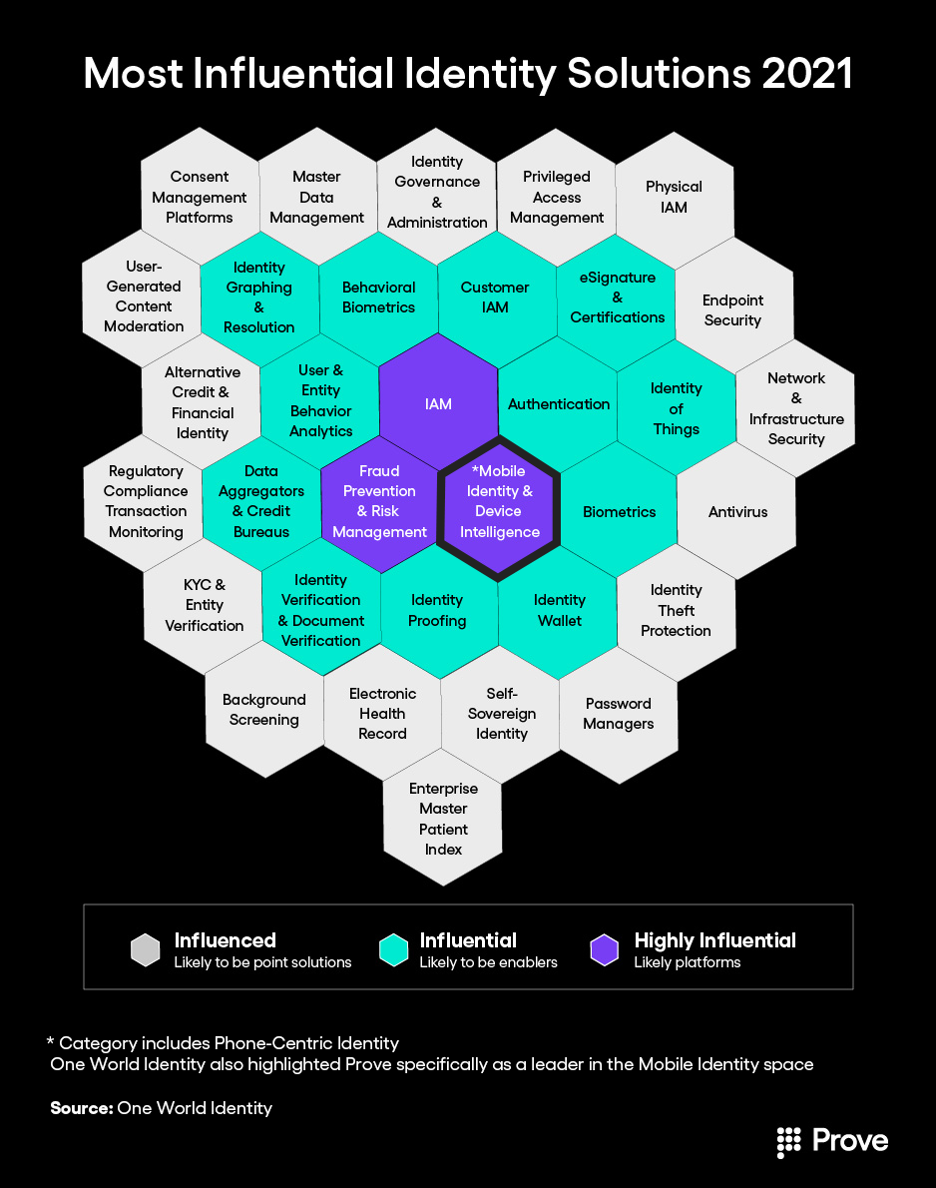
One World Identity, an authority in the digital identity space, recently highlighted Prove as a leader in digital identity and emphasized the efficacy and growing influence of the mobile approach: “Being able to rely on that device as a proxy for a human—especially a mobile device—because how many of us are attached at the hip to our smartphones all day every day? That makes this tremendously useful, especially for these fraud and risk use cases,” said Cameron D’Ambrosi, Managing Director of OWI.
Interested in learning how Prove’s Phone-Centric Identity technology can improve your identity verification strategies to make your customer experiences safer, faster, and easier? To request a demo or speak with an expert, click here.
About Prove
Prove is the modern platform for Phone-Centric Identity authentication, powering over 1,000 enterprises, including 500 financial institutions, leading Tier 1 UK banks, and 9 of the top 10 US financial institutions, across 195 countries. For the latest updates from Prove, follow us on LinkedIn.
Get in touch

Keep reading
.png) Read the article: The Crisis of Identity, Part 1: Why Agentic Commerce Needs a KYA Roadmap
Read the article: The Crisis of Identity, Part 1: Why Agentic Commerce Needs a KYA RoadmapAs AI agents begin transacting on behalf of humans, the lack of a unified identity standard is creating a trust crisis in agentic commerce, one that Prove’s Know Your Agent (KYA) framework aims to solve by securely linking every agent action back to a verified human.
 Read the article: Why Prove Matters When Identity Data Leaks Become Critical Infrastructure Failures
Read the article: Why Prove Matters When Identity Data Leaks Become Critical Infrastructure FailuresAs large-scale data breaches expose billions of identity records, traditional identity verification and KYC models fail under automated fraud, making cryptographically anchored, persistent digital identity critical infrastructure.
 Read the article: How Prove’s Global Fraud Policy Stops Phone-Based Fraud Others Miss
Read the article: How Prove’s Global Fraud Policy Stops Phone-Based Fraud Others MissLearn how Prove’s Global Fraud Policy (GFP) uses an adaptive, always-on engine to detect modern phone-based threats like recycled number fraud and eSIM abuse. Discover how organizations can secure account openings and recoveries without increasing user friction.













