How to Fight Account Takeover Fraud with Trust Score+™
.webp)

Firms have the power to protect consumers by investing in real-time phone signal technology that fortifies vulnerable One-Time Passwords (OTPs) and prevents Account Takeovers (ATOs).
ATOs are not a new fraud revelation; we all know what they are, but they don’t need to be normalized as a standard cost of doing business. In 2022 alone, ATOs hit 22% of US adults and represented nearly $288 billion in fraud, and T-Mobile alone was reported to have been breached over 100 times in ATO phishing attacks – “Three different cybercriminal groups claimed access to internal networks at communications giant T-Mobile… In each case, the goal of the attackers was the same: Phish T-Mobile employees for access to internal company tools, and then convert that access into a cybercrime service that could be hired to divert any T-Mobile user’s text messages and phone calls to another device.” If ATOs are so damaging, how are they allowed to still proliferate? The root problem lies with reliance on OTPs which are simple to deploy but have critical downsides – fraud vulnerability, consumer friction, and cost.
OTPs are vulnerable to critical telephony infrastructure exploits, and firms struggle to detect these gaps:
- SIM Swap: While legitimate SIM swaps allow customers to keep their phone numbers while switching carriers, hackers can use stolen PINs to SIM swap a victim’s phone without their knowledge or consent.
- Call Forwarding Scam: When a customer requests an OTP, they often choose to have the OTP sent via SMS or read to them over the phone (voice OTP). While voice OTPs are a great way to provide equitable service to visually impaired customers, fraudsters can also steal them using the call forwarding setting.
- Device Swap: A device swap is a simpler version of a SIM swap because it involves stealing the actual SIM card of a victim. A fraudster inserts the stolen SIM card into a new phone, enters the stolen PIN purchased from the dark web, and steals the OTPs to access the victim’s accounts.
The common thread between these methods: exploiting cybersecurity weaknesses in telephony infrastructure and stealing OTPs. While improving infrastructure is critical, it will require unprecedented cooperation between cellular carriers and government regulatory agencies and could take years to implement. In the meantime, companies must prevent ATOs by becoming more discerning about who should and who shouldn’t receive OTPs as well as understanding transaction-level risk…as it happens.
So what can businesses do today to stop Account Takeovers?
To prevent ATOs, companies need to secure OTPs by analyzing, in real-time, the trust level of a transaction through phone number intelligence and associated trust indicators - enter Prove’s Trust Score+TM. Trust Score+ leverages phone number signals from the core telephony infrastructure, proprietary data sources, and Prove’s 15+ years of phone data to identify risks based on the history of that phone number while pulling in Mobile Network Operator (MNO)/carrier data to track risky phone number behavior in real-time during high-risk events (e.g., money movement, password changes, phone number updates, etc.) to detect account takeover risk, identify device theft, unauthorized SIM swaps and ports, and more.
Key trust indicators that Trust Score+ taps into to detect and stop ATOs:
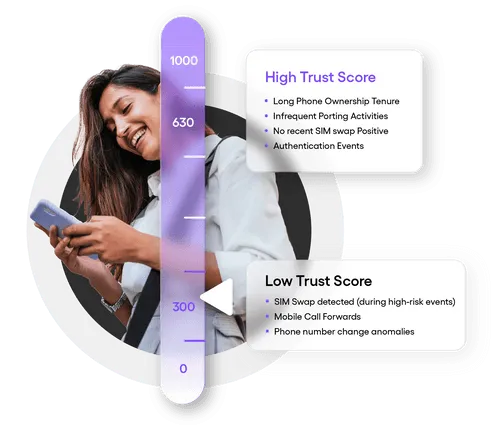
- SIM & Device Velocity: how many SIM or Device changes have been associated with a phone number?
- SIM Tenure: how long has this SIM been active?
- Call-Forwarding Enabled: has call-forwarding been enabled for this number?
High change event velocity, low SIM and device tenures and an out-of-the-ordinary call-forwarding setting on a phone number are red flags that indicate a potential account takeover and allow firms to deploy informed decisioning.
Interested in how other firms have benefitted from Trust Score? Learn how E*Trade and another growing FinTech stopped fraud while improving consumer experience.
_________________________________________________________________________
Leveraging Trust Score+™, companies can detect ATOs, and stop them in real-time. In order to cut down on fraud, protect customers, and strengthen business operations, companies must fortify their OTPs and decisioning protocols using phone-centric technology.
To learn more about Prove’s identity and authentication solutions and how to accelerate revenue while mitigating fraud, talk to an expert today.

Keep reading
 Read the article: Why Prove Matters When Identity Data Leaks Become Critical Infrastructure Failures
Read the article: Why Prove Matters When Identity Data Leaks Become Critical Infrastructure FailuresAs large-scale data breaches expose billions of identity records, traditional identity verification and KYC models fail under automated fraud, making cryptographically anchored, persistent digital identity critical infrastructure.
 Read the article: How Prove’s Global Fraud Policy Stops Phone-Based Fraud Others Miss
Read the article: How Prove’s Global Fraud Policy Stops Phone-Based Fraud Others MissLearn how Prove’s Global Fraud Policy (GFP) uses an adaptive, always-on engine to detect modern phone-based threats like recycled number fraud and eSIM abuse. Discover how organizations can secure account openings and recoveries without increasing user friction.
 Read the article: Prove Supports Safer Internet Day: Championing a Safer, More Trustworthy Digital World
Read the article: Prove Supports Safer Internet Day: Championing a Safer, More Trustworthy Digital WorldProve proudly supports the goals and initiatives behind Safer Internet Day, a worldwide effort that brings together individuals, organizations, educators, governments, and businesses to promote the safe and positive use of digital technology for all, especially young people and vulnerable users.












